NOTICE: This post references card features that have changed, expired, or are not currently available
This story involves an aging dog, the Google Search app, a Citibank credit card perk I’ve never before used, and the infamous Equifax Hack (for the latter, see: Is the Equifax cure worse than the hack?).
While doing research for my “Equifax Hack Rx” series, I learned how insecure SMS is for two factor authentication, and that led me to change security on my Gmail account. Did I lose you there? Let me back up… The main thing I’m worried about with the Equifax Hack is the likelihood that our personal information will be used by criminals to get access to our accounts: bank accounts, digital currency accounts (BitCoin, for example), frequent flyer accounts, etc. All they would need to do is to try to log into our accounts and click the “forgot password” link.
After clicking “forgot password” the criminal may have to answer some questions to prove that they are you. Well, thanks to the great security forces at Equifax, the criminal may now have the information needed to do just that. In many cases, though, the way a criminal must “prove” they are you is by receiving a text or email message containing a one-time code.
Regardless of whether the criminal must answer security questions or get access to a one time code, the end result if they are successful is a new one-time password sent by email.
If the criminal gets that one-time password, then they are in. Most financial institutions have additional safeguards to prevent people from suddenly cleaning out your account, and federal and state laws are likely to protect you anyway. But other forms of digital valuables are not so well guarded. Digital currencies like BitCoin can be instantly and irrevocably liquidated. And loyalty rewards (frequent flyer miles, store rewards, etc.) can often be cashed out quickly and easily as well.
All of this shows how critically important it is to safeguard your email account. A strong password isn’t enough. A hacker can use the “forgot password” exploit to still get in. For years, I thought that I had properly secured my Google Gmail accounts by enabling two-factor authentication. Anytime I logged into my Google account from a new device, Google would send me a code via SMS text message. The only way into my inbox was by entering that code. That’s safe right? No… it turns out that it’s not safe at all.
Just last week, Forbes published “All That’s Needed To Hack Gmail And Rob Bitcoin: A Name And A Phone Number“. Apparently it’s easy for an expert hacker to intercept text messages! The article describes a hacking demonstration by researchers from Positive. Here’s a summary quoted from the article:
In their attack, the Positive researchers first went to Gmail, using Google’s service to find an email account with just a phone number. Once the email account was identified, the hackers initiated a password reset process, asking one-time authorization codes to be sent to the victim’s phone. By exploiting SS7 weaknesses they were able to intercept text messages containing those codes, allowing them to choose a new password and take control of the Gmail account. They could then simply head to the Coinbase website and do another password reset using the email they’d compromised.
Yikes!
Fixing the hole where the hackers get in…
Immediately after reading this article, I browsed to my Google account (myaccount.google.com) and ran their Security Checkup. At the end, I had a chance to change my 2 Factor authentication settings. I removed my phone as an option and instead setup both Google’s Authenticator app and the Google prompt options. I installed the Google Authenticator app on my iPhone for the former, and installed the Google Search app to enable the latter.
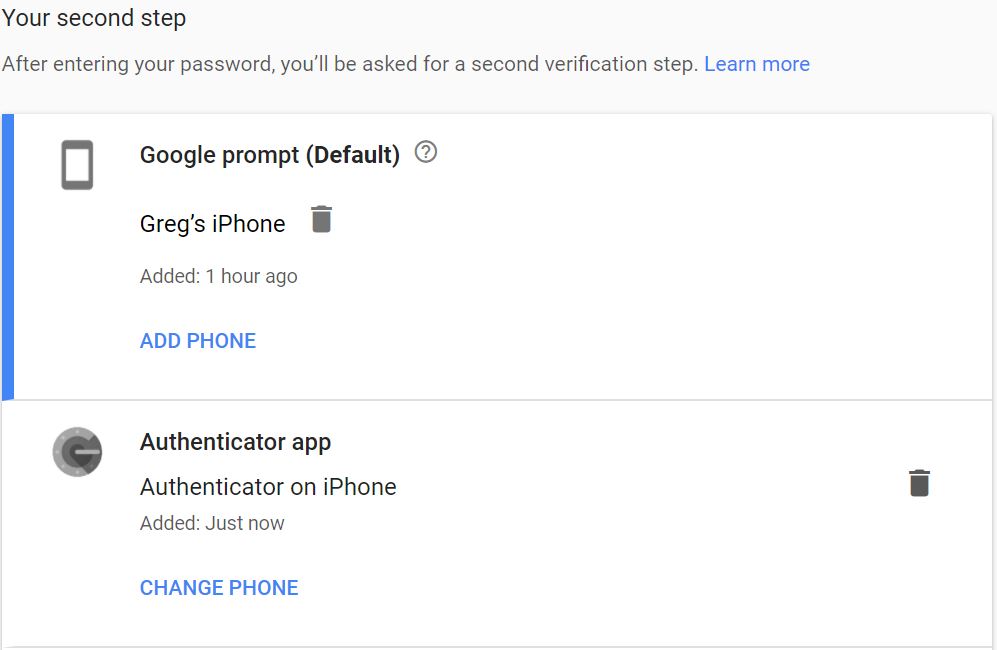
I’m sure that I’m nowhere near completely safe from hackers, but by changing my 2 factor authentication to less vulnerable options, I should be significantly safer than before.
How to setup 2-Step Verification with Google
|
About that Google Search app…
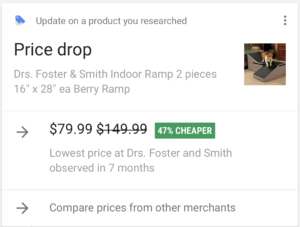
One of the things that the Google Search app can do is to hack your life… but in a good way (albeit creepy). Within minutes of installing the app, this alert popped up: “Update on a product you researched: Price drop”
When my dog isn’t busy photo bombing my credit card photo shoots, he spends his time getting older instead. We don’t know how old he is — he was a rescue — but we know from his behavior that his attempt to get older is working…



In addition to aging, our dog’s other favorite hobby is to sleep. And as he gets older, he has a tougher time each day jumping up to our bed. Even though he sleeps most of the day wherever he is around the house, nothing is as good as sleeping in bed. So we bought him foam doggie stairs that we found on Amazon. He hated them. Despite treats, goading and cajoling, he wouldn’t climb those stairs.
So, we tried a more expensive option: Drs. Foster & Smith Dura-Ruff® Indoor Ramp.

Well, it sort-of works. Our dog won’t use the ramp part of the thing at all, but he does jump to the midway point and from there jumps up to our bed. Mission accomplished (as long as he doesn’t get any older).
So… back to that Google price drop alert… I had paid $135, but the same ramp was now being advertised for $79.99. That’s a $55 difference.
I had paid for the ramp with a Citibank card. That was good news since Citi has a nice “Price Rewind” feature for all of their cards. Theoretically you can have Citi watch prices for you and automatically pay you when the price drops. In this case, Drs Foster & Smith products are apparently not in their search zone. Instead, I filled out a Price Rewind Benefit Request Form and emailed it to Citi. While they haven’t responded yet, I do expect to get the difference back.
As an aside: I probably should have contacted the online store’s customer support to see if they would refund the price difference directly. I was curious about using credit card price protection, though, so I decided to try out that benefit.
Wrap Up
All of the above was a long way of saying that you should do the following:
- You should setup two-factor authentication to protect your email accounts
- Whenever possible, don’t use SMS (phone texts) for two-factor authentication. Instead, use something like Google’s Authenticator app.and (less importantly):
- If you’re going to buy something that is likely to drop in price, use a credit card that has some form of price protection (many do).
- Consider allowing Google to mine your life (they’re doing it for good, right?)
- Do whatever it takes to make your dog happy.
See Also
- Is the Equifax cure worse than the hack?
- Complete Guide to Free Credit Scores, Reports, and Monitoring
- Equifax Hack Rx: Free Identity Theft Insurance
- Equifax Hack Rx: Free credit monitoring



Greg,
Thank you for this entire series! This has been the most comprehensive, informative advice I’ve read anywhere on how to play both offense and defense when it comes to protecting our identity/accounts. I’ve learned a lot and am far better prepared now.
This thread is way off the Frequent Miler core mission…and I hope you keep it open! It’s a valuable aid to us who are struggling with all the new lingo and authenticators etc.
I installed the LastPass Athenticator because I’m an LP Premium user. Nowhere does anyone tell me that I don’t need multiple authenticators…I started by installing Google Auth and LP Auth because I thought they both needed their own “authentication applications”. Makes sense, no? Well, now I have two Authenticators on my phone. Double your pleasure, double your fun…
That said, does anyone have experience with LastPass Authentication? So far I seem to have enabled it successfully, but I’m really confused about how it will change my user experience. Plus, I am trying to enable the LP Cloud Backup to over come the “smashed phone” issue, but LP’s Help Text is out of date and the prompts they say I should see on the phone are not there.
Ugh, this has consumed my whole morning. But thanks are due to Greg, Nick, Ed, MM, Earl, Dave, and all you others who are contributing to this thread.
[…] How the Equifax Hack scared me into installing Google Search and may have saved me $55 […]
Oh no doubt I wasn’t trying to argue that people shouldn’t be careful. Only that really people don’t know how bad it is out there and how much worse it will get. Even the big banks can’t stop it. I’ve had two new credit cards that I never used anywhere and the banks themselves got hacked and thieves already used the new cards.
This will perhaps be one of the biggest issues that we’ll deal with heading into the next decade.
Honestly if someone really wants to hack your computer (or life) they can do it and no amount of authentication will stop them. One of my friends used to work for the NSA back in the day. He told me about some of this stuff that Snowden spilled long ago! Scary stuff.
Morale of the story is that if someone really wants to hack you they will.
That’s true, but keep in mind that millions of accounts were likely exposed. Hackers will go after the easy marks first.. and there must be plenty of those. It’s like the joke about surviving a bear attack. You don’t have to run faster than the bear… you have to run faster than the person next to you.
Of course you’re right that if they want to hack you personally they probably will no matter what. But if they just want to hack *somebody*, are they going to go through the steps to hack someone who is more challenging or just take the low-hanging fruit? That’s the idea here. If someone wants to steal your car, they will. But I bet you probably don’t park it with the key in the ignition and the engine running with the door wide open and a neon sign saying “I’ll be back in two hours” — I bet you usually lock it up and bring the key with you instead. And that’s the idea here — Greg’s giving you tools to use to lock it up and keep it as safe as you can. By adding as many layers as you can, you’re at least adding a time cost that hopefully makes you a less attractive target (similar to people using The Club on their car or an alarm indicator — it’s not going to make your car impossible to steal, just less attractive than the one that is open and running).
Would anyone know if several different gmail accounts can be set up for Google Prompt on the same phone?
I am setting up 2 step authentication and am stuck on Google Prompt setup. I have already successfully set up one gmail account on this phone and am trying to do the same for second account. I am using the same cell phone as for the first account. I get the same screen and can’t get past this. The phone number is verified and is clearly visible.
Trying to figure out why I can’t proceed. Is this one account per phone issue? or something else? Thanks
I haven’t tried it yet. Did you log into your second gmail account on your phone? The Google Search app lets you setup multiple accounts that you can switch back and forth between. It would make sense to me that you’d have to be logged into the second account for prompts to work
I was signed in to the second account. But it acted like there was no phone number associated. I am trying the Authy now but haven’t figured it out yet.
FYI: Just tried Google Prompt on a second email and it worked fine.
Sorry I didn’t answer this earlier. I have several Gmail accounts on my phone (Android) and prompt automatically works on all of them. Any time I log in from a new device or location, I get a phone notification.
I am irritated that the Equifax hack is causing all of us so much angst, time, and effort. I appreciate this blog post very much.
In any event, I have set things up a little differently. Remember that all of us here love to travel. I own a separate unlocked GSM cell phone for travel, and I buy an inexpensive SIM card when I visit a new country so that I have a phone for emergencies. (My travel phone is not a smartphone.) I bring, but generally do NOT use, my Verizon cell phone when abroad. Also, I always travel with my laptop, and I keep the laptop files synchronized with my desktop files.
So I have set up Google Prompts and Google Authenticator. But I am concerned that when I am abroad and trying to sign in to Gmail using a hotel’s network, my Verizon cell phone from home might not work well for Prompts or Authenticator. So I also added Google Backup codes as a third thing that I could use for 2 factor verification to get into my Gmail account. Since I saved the Google Backup codes in my desktop PC, these will go into my laptop at the next sync. Therefore, if Prompts and Authenticator both fail while abroad, I will rely on the Backup codes to get into Gmail.
Am I understanding this stuff correctly, or am I screwing up somehow? This security stuff is a PITA.
One more thing… I’ll add something to my initial comment.
I will wager that many of us have more than one email account. I also use Yahoo Mail. Yahoo mail offers 2 step verification, but the verification options are not as robust as Google and appears only to be to your cell phone. I don’t see anything in Yahoo mail that would allow me to bypass the cell phone. So after initially turning 2 step verification ON for Yahoo, I have now turned it OFF because I have the same concern that I might have difficulty signing in from a hotel’s network when traveling abroad. I just don’t trust my USA Verizon cell phone to work reliably abroad and I could not figure out a non-cell phone path to 2 factor verification at Yahoo.
I used to use Google authenticator in the past, including for my bitcoin wallet. I loved it until I lost my phone with the authenticator app. I am not tech savvy, so take this with a grain of salt. All the sites I used google authenticator became extremely difficult to reset. It seemed like the authenticator code was tied to your device not your google account. So if you upgrade/loose or destroy your device it was difficult to reset. If its easier now, I will use it again.
There seem to be a number of things the hacker would need access to and that reduces the potential somewhat. Also wondering as the poster above did about voice calls. I may be the only reader with a landline, but that is harder to spoof than a cell phone. I vary authentication where I have it enabled, sometimes choosing voice line, sometimes text, sometimes email. I also own several domains so email gets routed and forwarded. I should get multiple warnings if there are attempts to change my email passwords and such.
Wondering also if POP would be safer than IMAP, realizing that not everyone has those options? I always laugh when a poster posts about using an email address as if everyone has just one! I must have twenty and they all have their purpose.
Trade-off is always security versus convenience.
I do Google my data from time to time to see what is out there in various databases.
Thanks for the post, always good to hear about threats.
Yep, there is definitely a trade-off between security and convenience. That said, Google prompt is arguably much more convenient than a code that you have to enter (all you have to do is click a button). But I think that having 2 factor auth setup at all is WAY better than not at all so if you prefer phone for some, that’s better than a password alone. Note that alerts about password changes might not help you if it happens while you’re sleeping.
I lean towards convenience, though that has sometimes meant cryptic Post-it notes. Low tech physical solutions trump virtual ones most of the time. I spents years using RSA keys, tokens and dongles along with 30 day passwords. If it takes too much mental effort, folks will find a more convenient solution. I also had the same Amazon password for twenty years!
I mentioned POP versus IMAP, because I find Email clients to be more robust and secure. I realize that wont work for a mobile lifestyle. Not putting years of email messages within reach of a hacker seems prudent in the same way as limiting what you share on social media. Just my two cents.
You are absolutely right about warnings that go bump in the night, but it’s the sum of all the little security measures that add up.
This is all such great info, thank you everyone.
When you say ” I do Google my data”, does that mean you do that using the Google Search app?
I am trying to figure out who is getting old? You or the dog?
Can you repeat?
Google Authenticator has horrible reviews.
That doesn’t matter if you only use it as a backup 2nd Factor option. It is considered very secure.
Maybe not a big deal to you, but I’m not particularly tech-savvy, and it sounds very user unfriendly. Backup or not, if it’s complicated and creates technical problems I am not equipped to solve, then I’ll look for some other solution. Possibly Authy.
I assume a phone call should also be secure? Google, via android, would not let me remove the phone number even though I set up my phone as above. However, I made it a phone call only. oe
A phone call is more secure than text, but a determined hacker can forward your phone so it’s not a perfect solution.
Darn, can’t figure out how to remove my phone from google as part of the two step authentication.
Start here: myaccount.google.com/signinoptions/two-step-verification
There should be a pencil icon next to the phone option. Click that and then click the Remove Phone button. At least that’s how it works from the Chrome browser on my laptop.
The problem with using a phone line (mobile) for 2 Factor Authentication is that someone can impersonate you either by calling into your carrier or going into the mobile store and hijack your line. This seems to be picking up steam where people will call in repeatedly until they get an operator who will give them access to your account and change your line to their sim card. This would be really easy to do when the Equifax data gets released since most carriers rely on data that Equifax had on file for verification. So if you have phone or text 2 FA enabled, they would be able to get into all your accounts if they hijacked your line. You wouldn’t know until you want to use your phone and saw you didn’t have service. Here’s an article on this: https://www.ftc.gov/news-events/blogs/techftc/2016/06/your-mobile-phone-account-could-be-hijacked-identity-thief
Greg, you should have gone a little further with your research! One of the biggest hidden problems with Google Authenticator happens when you change phones (e.g. if you lose it or upgrade) you have to plan ahead and most people don’t.
Authy is another (free) app that is 100% compatible with Google Authenticator and lets you backup and restore, plus access it from multiple devices. Just google it “authy vs google authenticator” It’s a must if you’re into cryptos and have accounts at places like coinbase, and works with gmail and any other place that mentions Google Authenticator.
Thanks! I look that up
Interesting. It looks like Authy does provide a more complete solution than Google Authenticator (but both are secure options). Interesting that Coinbase has gone against Authy, but it is unclear why:
http://www.newsbtc.com/2017/06/03/coinbase-recommends-users-enable-google-authenticator-ditch-authy/
I may switch to Authy. Need to do bit more research.
I see someone else mentioned a problem with the difficulties of a lost/broken phone with Google Authenticator also. I’m surprised. I admittedly didn’t use Google Authenticator for many things in the past, but I did have it on my previous phone, which I dropped and smashed and it wouldn’t work. I got a new phone and I do remember having to do something to switch over Authenticator to my new device, but whatever I did was easy enough that it’s not memorable. I’m not sure that’s a good thing in this context (after all, we don’t want it to be easy for a hacker either), but from the standpoint of switching devices I didn’t find it notably difficult. Again, I wasn’t using it with many accounts, so perhaps my experience is too limited to have come to know the broader issues. I’m going to be looking into this, too.
I added a section titled “How to setup 2-Step Verification with Google” to help clear up confusion from the original article. Hope that helps!
Aah, much clearer. Thank you. All set up for one, one a few, or more than a few to go.
Must say that I am confused too. This was all about Authenticator and the suddenly there was a search and I am still not following how to set up 2 step authentication. I will google it so I can find step by step.
Thanks for the warning and the pointers. Will definitely fix mine.